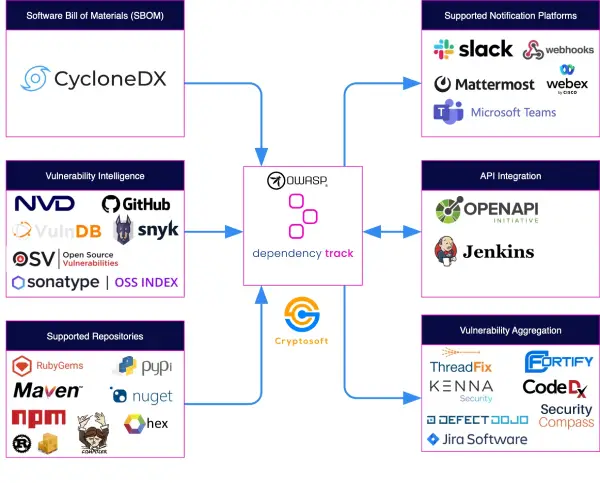
Cryptosoft OWASP® Dependency-Track’s features
SBOM creation services
We provide Github Actions and interfaces for traditional toolchains, like Jenkins, to create an SBOM for you from your source-code libraries. We also simplify the pushing of your created SBOM to our OWASP® Dependency-Track service for analysis. For more detail read here
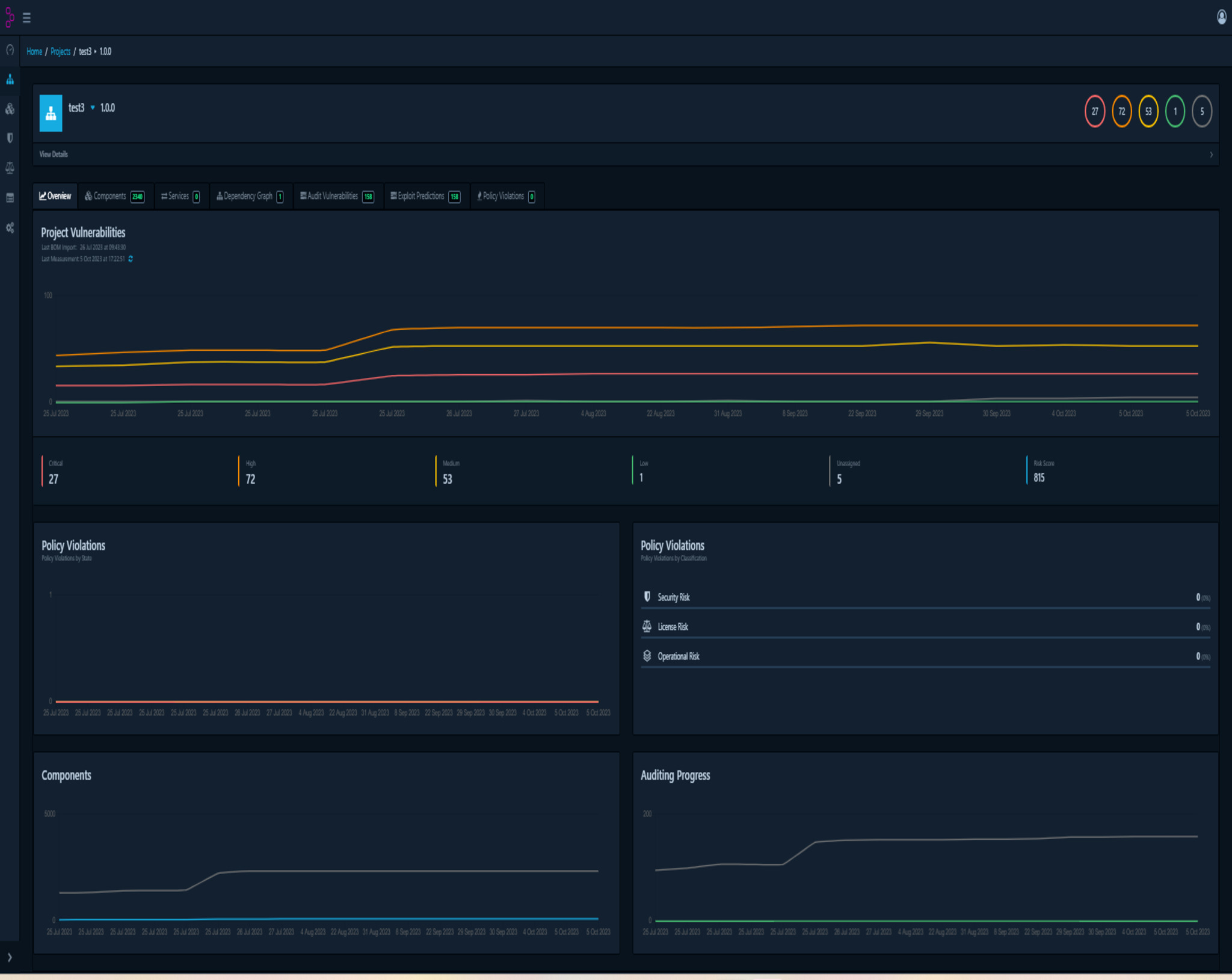
Security vulnerabilities
We expose security vulnerabilities, with their details and severity.
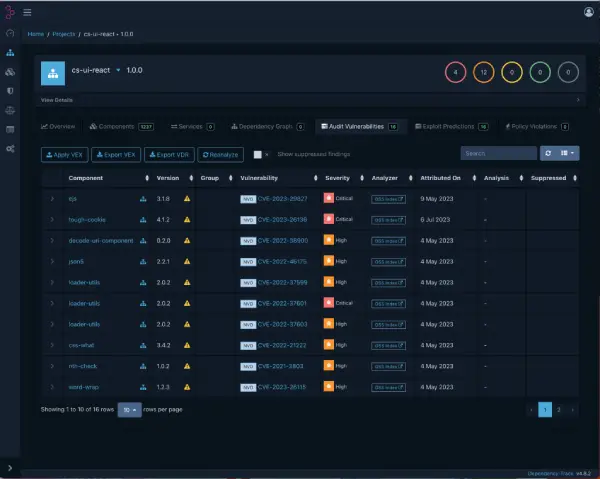
Open source software licensing
We identify potential licensing conflicts by showing the software licenses being used for components, or exposing where no license is being used.
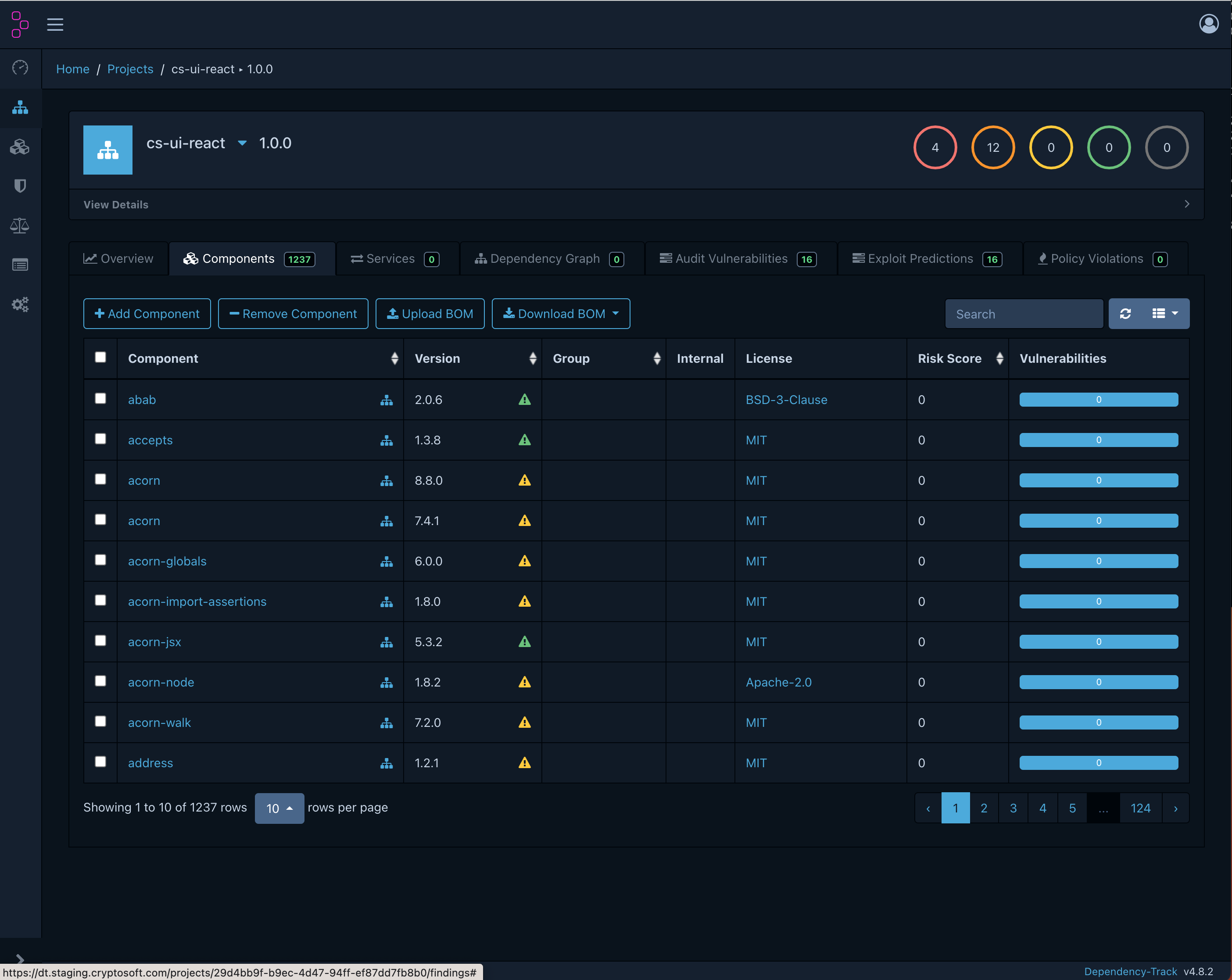
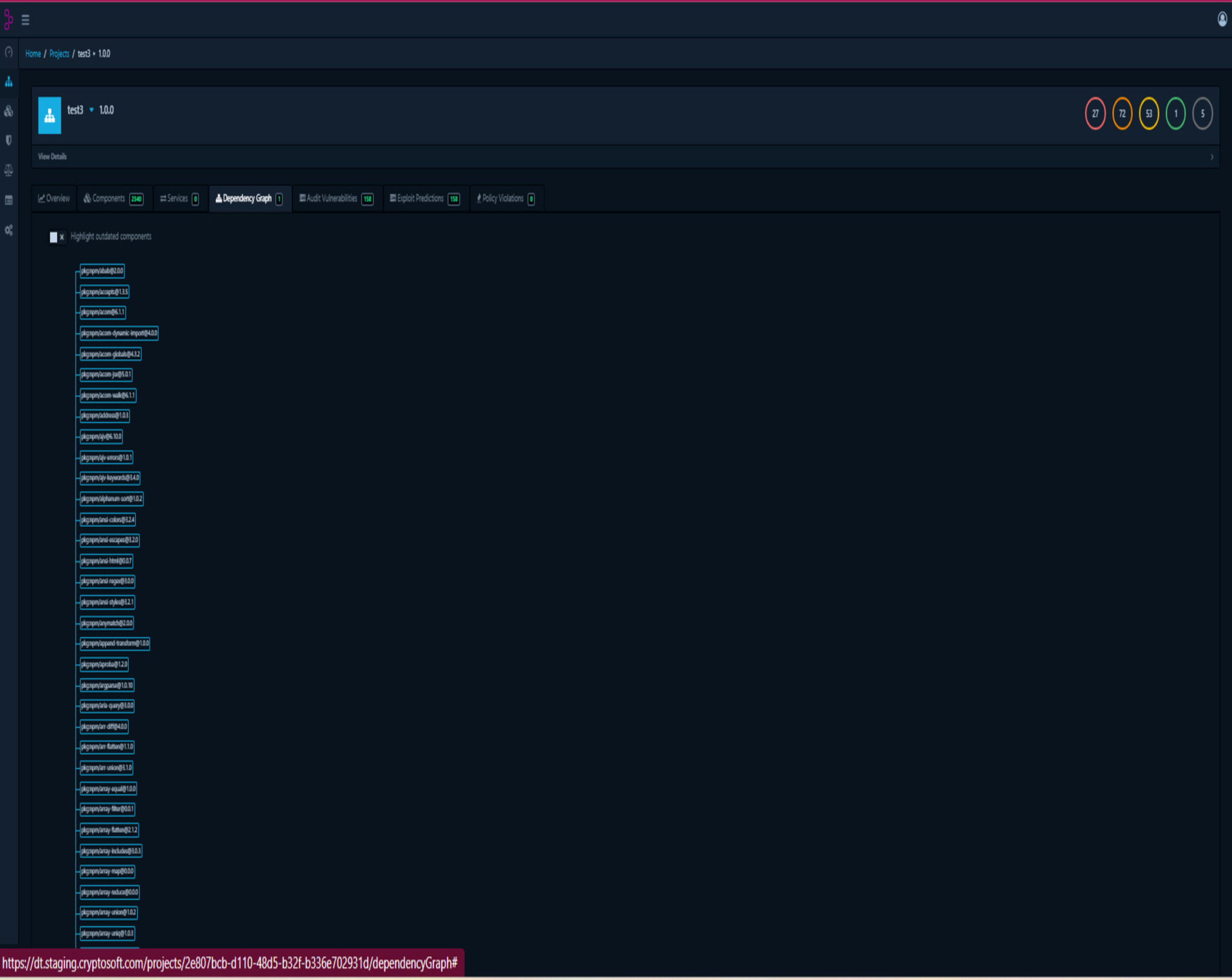
Understanding dependencies in your code
We help you understand which dependencies are related to which component.
Compliance with your security policy
We assess the SBOM against your security policy, highlighting policy violations and helping you build reports for audits.
Why Cryptosoft?
- We offer an end-to-end solution to all your SBOM needs from creation through analysis
- Our SaaS solution is based on the proven OWASP® Dependency-Track project
Reduced time to deployment
- Enterprises can quickly implement and start benefiting from our solution without prolonged setup phases.
Reliability
- Through leveraging a proven solution from OWASP®, a trusted entity in the security world, we ensure that best practices and trusted methodologies are used.
- The Cryptosoft team are proven expects in security, DevSecOps, SaaS management and delivering robust commercial solutions
Cost Savings
- Through a reduction in development costs and potential future remediation since the solution is already designed to address common and critical vulnerabilities.
- Savings in infrastructure and deployment management, allowing you to focus your skilled resources on more business orientated activities.
We offer deployment flexibility to implement as a SaaS or a private individual managed application behind your firewall
- Enterprises can choose the model that best fits their security, regulatory, and infrastructure needs.
- Support of your implementation by DevSecOps and managed services experts
CONTACT
Get In Touch